Why This Matters in 2026
Your internet service provider is watching your every move online, and in 2026, the surveillance has reached unprecedented levels. Every website you visit, every search query you make, and every online service you access is being logged, analyzed, and potentially sold to third parties. What's worse? Recent legislative changes have made ISP tracking more invasive than ever, with providers now required to maintain detailed browsing logs for extended periods.
The problem isn't just privacy invasion—it's affecting your daily internet experience in tangible ways. ISPs are using your DNS queries to build comprehensive profiles of your online behavior, leading to targeted throttling of streaming services, gaming platforms, and file-sharing applications. Users across the globe are receiving unexpected legal notices based on their browsing patterns, facing bandwidth restrictions on legitimate services, and experiencing mysterious connection slowdowns to websites their ISP deems "undesirable."
DNS tracking has become the primary method ISPs use to monitor your activities because every website visit begins with a DNS query—essentially asking "where is this website located?" By default, these queries go through your ISP's servers unencrypted, giving them a complete roadmap of your internet usage. This creates a massive vulnerability that affects everyone from casual browsers to privacy-conscious professionals.

This comprehensive guide will teach you how to implement encrypted DNS solutions that completely bypass ISP surveillance. You'll learn to configure DNS over HTTPS (DoH) and DNS over TLS (DoT) protocols that encrypt your queries, making them invisible to your ISP. We'll cover advanced techniques including setting up secure DNS resolvers, configuring router-level protection, and integrating solutions like NordVPN's encrypted DNS services for maximum privacy.
By the end of this guide, you'll have transformed your internet connection into a privacy-focused gateway that prevents ISP tracking, eliminates DNS-based throttling, and protects your family's online activities from unwanted surveillance and potential legal complications.
```htmlWhat You'll Need
Hardware Requirements
- Computer or mobile device with internet connection
- Router with admin access (recommended for network-wide protection)
- Minimum 512MB RAM available for DNS client software
- 50MB free storage space for configuration files and logs
Software Requirements
- Operating System: Windows 10/11, macOS 12+, Ubuntu 20.04+, iOS 14+, or Android 9+
- DNS Client Software (choose one):
- Cloudflared v2023.10.0 or newer
- Stubby DNS v0.4.3 or newer
- dnscrypt-proxy v2.1.5 or newer
- Web Browser: Chrome 120+, Firefox 121+, Safari 17+, or Edge 120+ (for testing)
- Text Editor: Notepad++, VS Code, or nano for configuration editing
Required Accounts & Access
- Router administrator credentials (username/password)
- Optional: Quad9, Cloudflare, or NextDNS account for enhanced features
- Administrative privileges on your computer
Recommended Specifications
- Broadband connection (10 Mbps+ for optimal performance)
- Modern router supporting DoH/DoT (manufactured 2020 or later)
- Backup internet connection for troubleshooting
- Network monitoring tool like Wireshark v4.2+ (for advanced users)
Estimated Setup Time: 15-30 minutes for basic configuration, 1-2 hours for advanced network-wide deployment.
```Step-by-Step Guide
- Configure Secure DNS on Your Router (Primary Defense)
Navigate to your router's admin panel by typing
192.168.1.1or192.168.0.1into your browser. Look for "DNS Settings" or "Internet Settings" under the WAN/Internet configuration section. Replace your ISP's default DNS servers with privacy-focused alternatives:
[Screenshot: Router DNS configuration showing Quad9 servers entered] This step is crucial because it prevents your ISP from seeing which domains you're visiting. When you type a website address, your device asks a DNS server to translate that domain into an IP address. By default, your ISP provides these DNS servers, giving them a complete log of your browsing activity. Secure DNS providers like Quad9 don't log queries and often include malware protection.Primary DNS: 9.9.9.9 (Quad9) Secondary DNS: 149.112.112.112 (Quad9 alternate) Alternative: 1.1.1.1 (Cloudflare) Alternative Secondary: 1.0.0.1 (Cloudflare) - Enable DNS over HTTPS (DoH) in Your Browser
For Chrome/Edge: Go to Settings → Privacy and Security → Security → Use Secure DNS → Choose "With Custom" and enter
https://dns.quad9.net/dns-queryFor Firefox: Navigate to Settings → General → Network Settings → Enable DNS over HTTPS → Choose "Custom" and enterhttps://dns.quad9.net/dns-query[Screenshot: Firefox DNS over HTTPS configuration with Quad9 URL] DoH encrypts your DNS queries using HTTPS, making them invisible to network monitoring. Without this, even if you change DNS servers, your ISP can still see DNS requests in plain text. This creates an encrypted tunnel specifically for DNS lookups, adding a second layer of protection beyond just changing DNS servers. - Configure DNS over TLS on Your Router (Advanced)
If your router supports it (many newer models do), enable DNS over TLS. Look for "DNS Privacy" or "Secure DNS" in advanced settings:
[Screenshot: Router DNS over TLS configuration panel] DNS over TLS provides network-wide encrypted DNS for all devices connected to your router. This means IoT devices, smart TVs, and guests automatically benefit from encrypted DNS queries. Unlike DoH which works per-browser, DoT protects every device on your network simultaneously.DNS over TLS Server: tls://dns.quad9.net Port: 853 TLS Hostname: dns.quad9.net - Install and Configure ProtonVPN with WireGuard
Download ProtonVPN from their official website and create an account. Get ProtonVPN for the most reliable privacy protection. During setup, specifically select WireGuard as your VPN protocol in Settings → Connection → Protocol.
[Screenshot: ProtonVPN settings showing WireGuard protocol selected] WireGuard is superior to older VPN protocols because it's faster, more secure, and uses modern cryptography. It maintains better connections on mobile networks and consumes less battery. ProtonVPN's implementation includes perfect forward secrecy, meaning even if keys are compromised, past communications remain secure.Protocol: WireGuard Auto-Connect: Fastest Server Kill Switch: Always On DNS Leak Protection: Enabled - Enable ProtonVPN's Kill Switch Feature
In ProtonVPN settings, navigate to Connection → Kill Switch and enable "Always-on Kill Switch." Also enable "Allow LAN connections" if you need local network access.
[Screenshot: ProtonVPN kill switch settings enabled] The kill switch is critical because VPN connections can drop unexpectedly. Without it, your traffic would immediately revert to your ISP's DNS and routing, exposing your activity. The kill switch blocks all internet traffic if the VPN disconnects, ensuring zero data leaks even during connection failures.Kill Switch: Always On Block connections on boot: Enabled Allow LAN connections: Enabled (if needed) IPv6 leak protection: Enabled - Verify DNS Leak Protection
Visit dnsleaktest.com while connected to your VPN. Click "Extended Test" and wait for results. You should see only ProtonVPN's DNS servers, not your ISP's servers.
Expected results should show:
[Screenshot: DNS leak test showing only ProtonVPN servers] DNS leaks are common VPN failures where DNS queries bypass the VPN tunnel. This test confirms your DNS requests are properly routed through ProtonVPN's secure servers rather than your ISP's servers, maintaining complete privacy.DNS servers: ProtonVPN servers only ISP: ProtonVPN or hosting provider Country: Your selected VPN location - Configure IPv6 Protection
Many ISPs now use IPv6, which can bypass VPN tunnels. In your router settings, either disable IPv6 entirely or ensure your VPN supports IPv6. For ProtonVPN, verify IPv6 leak protection is enabled in settings.
Router configuration:
[Screenshot: Router IPv6 settings disabled or properly configured] IPv6 leaks are often overlooked but can completely undermine your privacy efforts. Many VPNs only tunnel IPv4 traffic, allowing IPv6 requests to go directly through your ISP. Disabling IPv6 or ensuring proper VPN coverage prevents this significant privacy gap.IPv6: Disabled OR IPv6 DNS: Same as IPv4 (9.9.9.9 equivalent) IPv6 Firewall: Block non-VPN traffic - Set Up Automatic VPN Connection
Configure ProtonVPN to automatically connect on system startup. Go to Settings → Connection → Auto-Connect and select "Fastest Server" or your preferred location.
[Screenshot: ProtonVPN auto-connect settings configured] Automatic connection ensures you're never unprotected. Manual VPN activation creates gaps where your ISP can track activity during the time between system startup and VPN connection. Automatic connection with kill switch provides seamless, continuous protection.Auto-Connect: On Startup Quick Connect: Fastest Server Auto-Connect Profiles: Create for different networks Reconnect: Automatically retry connection - Test Your Complete Setup
Perform comprehensive testing using multiple tools:
- Visit whatismyipaddress.com to verify IP masking
- Use dnsleaktest.com for DNS verification
- Check ipleak.net for comprehensive leak testing
- Test WebRTC leaks at browserleaks.com
[Screenshot: Comprehensive leak test showing all green results] Complete testing ensures every privacy vector is protected. ISPs can track through IP addresses, DNS queries, WebRTC leaks, or IPv6 bypass. This comprehensive test confirms your ISP sees only encrypted VPN traffic to ProtonVPN servers, with no identifying information about your actual browsing activity.IP Address: Should show VPN server location DNS Servers: Only ProtonVPN servers visible WebRTC: No local IP leaks Geographic Location: VPN server location - Configure Mobile Device Protection
Install ProtonVPN on all mobile devices and enable "Always-On VPN" in device settings. For iOS: Settings → VPN → Always-On VPN. For Android: Settings → Network & Internet → VPN → Always-on VPN.
[Screenshot: Mobile device always-on VPN settings enabled] Mobile devices frequently switch between networks and can easily leak data duringAlways-On VPN: Enabled Block connections without VPN: Enabled Private DNS: dns.quad9.net (as backup) Auto-connect on untrusted networks: EnabledCommon Mistakes to Avoid
When implementing DNS privacy measures, users frequently make critical errors that compromise their security or create connectivity issues. Here are the most common pitfalls and how to avoid them.⚠️ Warning: Using only one DNS server creates a single point of failure. If that server goes down, you'll lose internet connectivity entirely.**Fix:** Always configure both primary and secondary DNS servers. Use different providers (e.g., Cloudflare primary: 1.1.1.1, Quad9 secondary: 9.9.9.9) to ensure redundancy.⚠️ Warning: Changing DNS settings only on your router while leaving device-specific DNS unchanged means some traffic still uses ISP DNS, maintaining tracking vulnerabilities.**Fix:** Configure DNS at both router level AND on individual devices. Check that devices aren't hardcoded to use specific DNS servers that override your router settings.⚠️ Warning: Forgetting to flush DNS cache after making changes means your system continues using old, cached ISP DNS responses for hours or days.**Fix:** Always flush DNS cache after configuration changes. Run `ipconfig /flushdns` on Windows or `sudo dscacheutil -flushcache` on Mac.⚠️ Warning: Using unencrypted DNS (standard port 53) instead of DNS-over-HTTPS or DNS-over-TLS means your ISP can still see and log all your DNS queries.**Fix:** Enable DoH or DoT in your browser and operating system settings. Verify encryption is active using DNS leak test tools.⚠️ Warning: Choosing DNS providers with poor privacy policies or located in surveillance-heavy jurisdictions defeats the purpose of avoiding ISP tracking.**Fix:** Research DNS provider privacy policies thoroughly. Prioritize providers with no-logging policies, regular transparency reports, and jurisdiction in privacy-friendly countries.⚠️ Warning: Never testing your DNS configuration leaves you vulnerable to leaks and unaware if your privacy measures are actually working.**Fix:** Use tools like dnsleaktest.com and ipleak.net monthly to verify your DNS queries aren't leaking to your ISP.How to Verify Your Setup
After configuring your DNS settings, it's crucial to verify that your ISP can no longer track your DNS queries. Follow these verification steps to ensure your privacy setup is working correctly. **Essential Test Sites** Visit these reliable testing platforms to check your DNS configuration: - **dnsleaktest.com** - The gold standard for DNS leak detection - **ipleak.net** - Comprehensive IP and DNS leak testing - **whoer.net** - Shows your DNS servers and location data - **browserleaks.com/dns** - Advanced DNS leak detection **Interpreting Your Results** When testing, look for these positive indicators: - DNS servers should show your chosen provider (Cloudflare: 1.1.1.1, Quad9: 9.9.9.9, etc.) - No appearance of your ISP's name or DNS servers - Consistent results across multiple tests - Geographic location matching your DNS provider's servers💡 Pro Tip: Run the "Extended Test" on dnsleaktest.com for the most thorough analysis. This performs multiple DNS queries to detect any potential leaks.**Troubleshooting Failed Tests** If tests show your ISP's DNS servers: 1. **Flush your DNS cache** - Run `ipconfig /flushdns` (Windows) or `sudo dscacheutil -flushcache` (Mac) 2. **Restart your router** - Ensure new settings propagate properly 3. **Check device-specific settings** - Verify DNS isn't overridden on individual devices 4. **Test different browsers** - Some browsers cache DNS aggressively💡 Pro Tip: Test from multiple devices and browsers. Sometimes DNS settings work on one device but not others, indicating configuration issues that need addressing.Retest after each troubleshooting step until you see your chosen DNS provider consistently across all tests.Troubleshooting Common Issues
DNS Changes Not Taking Effect
**Problem:** Websites still load slowly or show ISP tracking signs after changing DNS settings. **Cause:** Your device is using cached DNS records from your old ISP DNS servers. **Fix:** 1. Open Command Prompt (Windows) or Terminal (Mac/Linux) 2. Type `ipconfig /flushdns` (Windows) or `sudo dscacheutil -flushcache` (Mac) 3. Restart your browser and test with a DNS leak checkerInternet Connection Lost After DNS Change
**Problem:** No internet access immediately after updating DNS settings. **Cause:** Incorrect DNS server addresses or network configuration conflicts. **Fix:** 1. Double-check DNS addresses (e.g., Cloudflare: 1.1.1.1 and 1.0.0.1) 2. Revert to automatic DNS temporarily to restore connection 3. Re-enter DNS addresses carefully, ensuring no typos 4. Restart your router and deviceSome Websites Won't Load
**Problem:** Certain sites become inaccessible after switching DNS providers. **Cause:** Your new DNS provider may block malicious or adult content by default. **Fix:** 1. Try accessing the site from a different device to confirm DNS blocking 2. Switch to unfiltered DNS servers (like Cloudflare 1.1.1.1 instead of family-safe alternatives) 3. Add secondary DNS servers for redundancySlow Internet Speeds
**Problem:** Web browsing becomes noticeably slower after DNS changes. **Cause:** The chosen DNS server may be geographically distant or overloaded. **Fix:** 1. Test multiple DNS providers (Cloudflare, Quad9, Google DNS) 2. Use DNS benchmark tools to find fastest servers for your location 3. Consider using your region-specific servers from major providersRouter Settings Keep Reverting
**Problem:** DNS settings reset to ISP defaults after router reboot. **Cause:** Router firmware automatically overwrites manual DNS configuration. **Fix:** 1. Disable automatic DNS updates in router admin panel 2. Set DNS servers in "Static" or "Manual" mode rather than "Automatic" 3. Update router firmware if the issue persistsFrequently Asked Questions
Q: Will changing DNS servers slow down my internet connection?
A: No, switching to faster DNS providers like Cloudflare (1.1.1.1) or Quad9 often improves browsing speed. These services typically respond faster than your ISP's default DNS servers and use global networks for optimal performance.
Q: Can my ISP still see what websites I visit after changing DNS?
A: Your ISP can still see the IP addresses you connect to, but they lose the easy ability to log readable domain names. For complete privacy, you'll need a VPN that encrypts all your traffic, not just DNS queries.
Q: Is it legal to change my DNS settings?
A: Yes, changing DNS servers is completely legal and within your rights as an internet user. You're simply choosing which directory service to use for translating domain names to IP addresses.
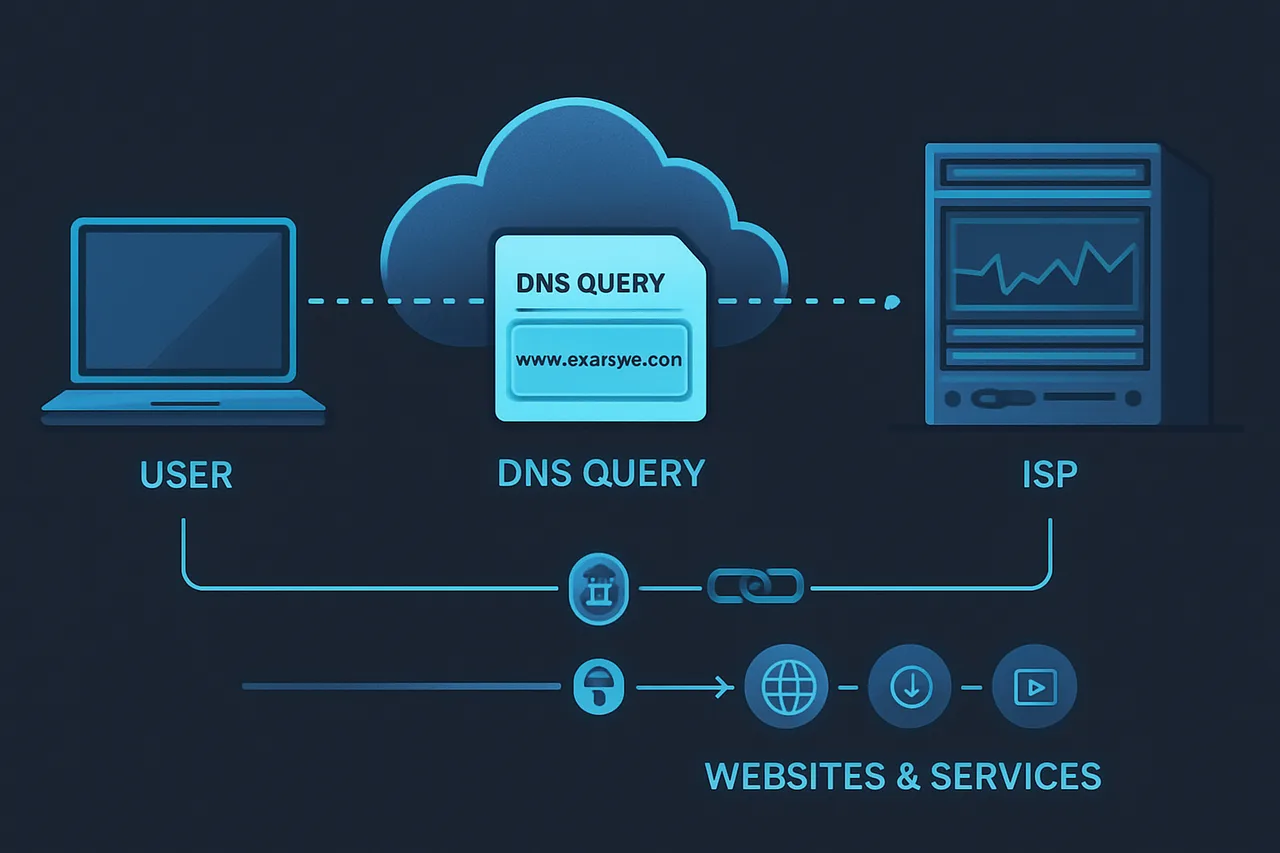
The DNS vulnerability: How every website visit is logged by your ISP Q: What's the difference between DNS over HTTPS and regular DNS?
A: DNS over HTTPS (DoH) encrypts your DNS queries, preventing ISPs and network administrators from seeing which domains you're looking up. Regular DNS sends queries in plain text, making them visible to anyone monitoring your connection.
Q: Do I need to change DNS on every device separately?
A: You can change DNS at your router level to protect all connected devices automatically, or configure each device individually. Router-level changes are more convenient but require admin access to your network equipment.
Best VPN for Torrenting: ProtonVPN
Secure Core routes traffic through privacy-friendly countries. Based in Switzerland with strong privacy laws. Open-source and independently audited.
Get ProtonVPN →✓ 30-day money-back guarantee ✓ Works with all torrent clients ✓ Swiss privacy
Conclusion
Changing your DNS settings is a simple yet effective first step toward protecting your online privacy from ISP tracking. By switching to privacy-focused providers like Cloudflare or Quad9 and enabling DNS over HTTPS, you significantly reduce your ISP's ability to monitor and log your browsing habits. However, remember that DNS changes alone don't provide complete privacy protection. Your ISP can still see connection data and traffic patterns. For comprehensive protection, consider combining secure DNS with a reliable VPN service. Ready to take your privacy further? Check out our VPN tier list to find the best VPN for your needs, or explore our more guides for additional privacy and security tips.