Why This Matters in 2026
In 2026, the digital surveillance landscape has reached unprecedented levels of sophistication. ISPs now deploy advanced deep packet inspection (DPI) technologies that can analyze network traffic in real-time, making torrent activity more visible than ever before. With recent legislative changes and increased pressure from copyright holders, understanding what your internet service provider actually sees when you torrent isn't just about privacy—it's about protecting yourself from legal consequences and maintaining your digital freedom.
The stakes have never been higher. Modern ISP monitoring systems can detect BitTorrent protocols within seconds of connection establishment, even when users attempt basic obfuscation techniques. What many users don't realize is that their ISP can see far more than just the fact that they're torrenting—they can identify specific files, track download progress, monitor peer connections, and even detect the torrent client being used.
This creates real-world problems that affect millions of users daily. ISPs routinely send DMCA takedown notices that can result in service termination after multiple violations. Bandwidth throttling has become increasingly aggressive, with some providers automatically limiting speeds by up to 90% when P2P traffic is detected. Beyond legal issues, unprotected torrenting exposes users to malware-infected files and potential security breaches that can compromise entire home networks.
This comprehensive guide will demystify the technical mechanisms behind ISP surveillance, explaining exactly what data packets reveal about your torrenting activities. You'll learn how deep packet inspection works at the protocol level, why standard proxy services fail against modern detection methods, and how advanced encryption technologies like those used by NordVPN and other enterprise-grade VPN services can effectively mask your activities.
More importantly, we'll provide actionable strategies to protect your privacy while torrenting, covering everything from proper VPN configuration to understanding the legal implications of P2P file sharing in your jurisdiction. By the end of this guide, you'll have the technical knowledge needed to make informed decisions about your torrenting practices.
What You'll Need
Before diving into ISP monitoring techniques and detection methods, ensure you have the following setup:
Hardware Requirements
- Computer with at least 8GB RAM and 2GB free storage
- Network adapter capable of promiscuous mode (most built-in adapters work)
- Router with DD-WRT, OpenWrt, or pfSense support (optional but recommended)
- Secondary device for testing (smartphone, tablet, or spare computer)
Software Requirements
- Wireshark 4.0+ - Primary packet analysis tool
- qBittorrent 4.5+ or Transmission 3.0+ - For generating torrent traffic
- VirtualBox 7.0+ or VMware Workstation 17+ - For isolated testing environments
- Nmap 7.90+ - Network discovery and port scanning
- Python 3.9+ with pip - For custom analysis scripts
- Web browser with developer tools (Chrome 110+, Firefox 110+)
Network Access & Accounts
- Administrative access to your home router
- VPN service account (ExpressVPN, NordVPN, or Mullvad recommended)
- Access to a seedbox or VPS (optional, for advanced testing)
Knowledge Prerequisites
- Basic understanding of TCP/IP networking
- Familiarity with command-line interfaces
- Understanding of how BitTorrent protocol works
- Basic networking troubleshooting skills
Note: This guide is for educational purposes only. Always comply with local laws and your ISP's terms of service.
Step-by-Step Guide
Understanding what your ISP sees when you torrent requires examining both unprotected and protected scenarios. This comprehensive guide walks you through monitoring your own network traffic to reveal exactly what data is exposed, then demonstrates how proper VPN configuration eliminates ISP visibility.- Set Up Network Traffic Monitoring First, install Wireshark to capture and analyze your network traffic. Download it from wireshark.org and install with default settings. Launch Wireshark and select your active network interface (usually "Ethernet" or "Wi-Fi"). Click the blue shark fin icon to start capturing packets. [Screenshot: Wireshark interface with network adapter selected and capture running] This step is crucial because it allows you to see exactly what data leaves your computer - the same metadata your ISP can observe. Without this visibility, you're operating blind to your actual privacy exposure.
- Configure Your Torrent Client for Monitoring
Open your torrent client (we'll use qBittorrent as an example) and navigate to Tools > Options > Connection. Note your current port number, then change it to a specific port like 6881 for easier identification in traffic analysis. Under "Listening Port," uncheck "Use UPnP/NAT-PMP port forwarding from my router."
[Screenshot: qBittorrent connection settings showing port 6881 configured] Setting a fixed port helps you identify torrent traffic in Wireshark captures. This demonstrates how ISPs can easily flag torrent activity by monitoring common BitTorrent ports and protocols.Connection Settings: Port used for incoming connections: 6881 Use UPnP/NAT-PMP: Disabled Use different port on each startup: Disabled - Download a Legal Test Torrent (Unprotected)
Download a legal torrent file such as a Linux distribution (Ubuntu is ideal). Add it to your torrent client and begin downloading. In Wireshark, apply the filter
tcp.port == 6881 or bittorrentto isolate torrent traffic. [Screenshot: Wireshark showing filtered BitTorrent protocol packets with visible IP addresses] This reveals the first major privacy concern: your real IP address is broadcast to every peer in the swarm. ISPs can see these connections and immediately identify BitTorrent protocol usage through deep packet inspection (DPI). The unencrypted handshakes contain protocol identifiers that automated monitoring systems easily detect. - Analyze Exposed Metadata Without VPN
In Wireshark, examine the captured packets. Right-click any packet and select "Follow > TCP Stream" to see the raw data exchange. Look for the BitTorrent protocol header (starts with "\x13BitTorrent protocol") and info_hash values.
This analysis shows that ISPs don't need to see file contents to identify torrenting. The protocol signatures, connection patterns, and peer IP ranges create an unmistakable fingerprint that automated monitoring systems flag instantly.Visible to ISP without VPN: - Your real IP address: 192.168.1.100 (example) - Destination peer IPs: Multiple worldwide - Protocol: BitTorrent (clearly identifiable) - Port usage: 6881 (common torrent port) - Connection timing and frequency patterns - Install and Configure ProtonVPN with WireGuard
Get ProtonVPN and install their official client. After creating your account, open the ProtonVPN app and navigate to Settings > Connection. Select "WireGuard" as your VPN protocol instead of the default OpenVPN.
[Screenshot: ProtonVPN settings showing WireGuard protocol selected] WireGuard offers superior performance for torrenting due to its lightweight code and faster connection establishment. Unlike OpenVPN's complex handshake process, WireGuard maintains consistent speeds under heavy torrent loads while using less CPU resources.ProtonVPN Recommended Settings: Protocol: WireGuard Kill Switch: Enabled DNS Leak Protection: Enabled Split Tunneling: Disabled - Enable Kill Switch Protection In ProtonVPN settings, locate "Kill Switch" and enable it. This critical feature blocks all internet traffic if the VPN connection drops unexpectedly. Test this by connecting to a VPN server, starting a download, then manually disconnecting the VPN. [Screenshot: ProtonVPN kill switch enabled in settings with warning dialog] The kill switch prevents catastrophic privacy leaks during VPN reconnections. Without this protection, your torrent client might continue downloading using your real IP address during connection interruptions, exposing your identity to ISPs and copyright monitoring systems.
- Connect to VPN and Verify IP Change
Connect to a ProtonVPN server (preferably P2P-optimized servers in Netherlands or Switzerland). Visit whatismyipaddress.com to confirm your IP has changed. In your torrent client, go to Help > About or check the status bar to see if it displays your new VPN IP.
This verification ensures your torrent traffic routes through the VPN tunnel. Many users assume they're protected without confirming the IP change, leaving them exposed to ISP monitoring.IP Verification Checklist: ✓ Browser shows VPN server IP ✓ Torrent client reflects new IP ✓ No DNS leaks detected ✓ WebRTC leaks blocked - Restart Torrent with VPN Protection
Stop your previous torrent download completely, then restart it with VPN connected. In Wireshark, clear previous captures and start a new capture session. Apply the same filter:
tcp.port == 6881 or bittorrent. [Screenshot: Wireshark showing encrypted VPN tunnel traffic instead of clear BitTorrent packets] Notice the dramatic difference: instead of clear BitTorrent protocol packets, you'll see encrypted tunnel traffic to your VPN server's IP. Your ISP can only observe encrypted data flowing to the VPN provider, not the underlying torrent activity. - Analyze VPN-Protected Traffic
Examine the new Wireshark capture. You'll see encrypted packets flowing to your VPN server's IP address using WireGuard protocol (UDP port 51820 by default). Try to follow the TCP stream - the data appears as encrypted gibberish.
This demonstrates perfect privacy: your ISP sees only encrypted tunnel traffic to a VPN server. They cannot identify torrenting, determine what files you're downloading, or see peer connections.ISP Visibility with VPN: - Destination: VPN server IP only - Protocol: WireGuard/encrypted tunnel - Content: Completely encrypted - Peer connections: Hidden within tunnel - Torrent signatures: Completely obscured - Test DNS Leak Protection Visit dnsleaktest.com while connected to ProtonVPN and run the extended test. Ensure all DNS queries route through ProtonVPN's servers, not your ISP's DNS servers. Any ISP DNS servers appearing indicate a privacy leak. [Screenshot: DNS leak test showing only ProtonVPN DNS servers] DNS leaks can expose your torrenting activity even with VPN protection. If your ISP's DNS servers appear in leak tests, they can log torrent tracker queries and piece together your downloading habits despite encrypted traffic.
- Configure Torrent Client DNS Settings
In qBittorrent, go to Tools > Options > Advanced. Find "Network Interface" and select your VPN adapter (usually "ProtonVPN TAP" or similar). This forces the torrent client to use only the VPN connection.
[Screenshot: qBittorrent advanced settings showing VPN adapter selected] Binding your torrent client to the VPN interface provides an additional layer of protection. If the VPN disconnAdvanced qBittorrent Settings: Network Interface: ProtonVPN TAP Adapter Resolve peer countries: Disabled Resolve peer host names: DisabledCommon Mistakes to Avoid
Understanding what ISPs can see is crucial, but many users make critical errors that expose their torrenting activities. Here are the most common mistakes and how to avoid them.⚠️ Warning: Torrenting without a VPN exposes your real IP address to all peers in the swarm and makes your traffic visible to your ISP through deep packet inspection.**The Fix:** Always use a reputable VPN service that doesn't log activity and supports P2P traffic. Verify your IP has changed before starting any torrent client.⚠️ Warning: Using free VPNs or proxy services often results in DNS leaks, unreliable connections, and some providers actually log and sell user data.**The Fix:** Invest in a paid VPN service with a proven no-logs policy. Test for DNS leaks using online tools and configure your torrent client to bind only to the VPN interface.⚠️ Warning: Leaving torrents seeding indefinitely increases exposure time and the likelihood of being detected by copyright monitoring services that join swarms.**The Fix:** Set reasonable seed ratios (typically 1.0-2.0) and time limits. Remove completed torrents from your client when you're done sharing.⚠️ Warning: Ignoring DMCA notices or thinking they're fake can lead to service termination, legal action, and escalating penalties from your ISP.**The Fix:** Take all copyright notices seriously. Document them, stop the infringing activity immediately, and consider consulting legal counsel if you receive multiple notices.⚠️ Warning: Using default torrent client settings often enables features like DHT, PEX, and local peer discovery that can bypass your VPN protection.**The Fix:** Disable DHT, PEX, and local peer discovery in your client settings. Configure your client to only connect through your VPN and enable the kill switch feature.⚠️ Warning: Torrenting copyrighted content from public trackers makes you an easy target for monitoring companies that actively join these swarms to collect IP addresses.**The Fix:** Consider using private trackers with better security practices, or stick to legal torrents of open-source software, public domain content, and Creative Commons materials.How to Verify Your Setup
Before torrenting, it's crucial to verify that your privacy tools are functioning correctly. A single misconfiguration can expose your real IP address to ISPs and copyright monitors. **Essential Test Sites** Start with **ipleak.net**, which provides comprehensive testing for IP, DNS, and WebRTC leaks. This single tool checks multiple potential exposure points simultaneously. **dnsleaktest.com** offers focused DNS leak testing with both standard and extended options. For additional verification, use **whatismyipaddress.com** to confirm your apparent location matches your VPN server. **Interpreting Results** Your displayed IP address should match your VPN server's location, not your actual geographic area. DNS servers should belong to your VPN provider or chosen DNS service—never your ISP. WebRTC tests should show no local IP addresses. Any appearance of your real IP or ISP's DNS servers indicates a dangerous leak.💡 Pro Tip: Test from multiple browsers and devices. Some configurations work in one browser but fail in others due to different WebRTC implementations.**Troubleshooting Failed Tests** If tests reveal leaks, immediately disconnect from any torrent clients. For IP leaks, verify your VPN connection and check for kill switch activation. DNS leaks often require manually configuring DNS servers in your network settings. WebRTC leaks need browser-specific fixes—disable WebRTC in Firefox or use Chrome extensions like WebRTC Leak Prevent. **Ongoing Verification** Test your setup weekly and immediately after any software updates. VPN clients, browser updates, or system changes can break previously working configurations.💡 Pro Tip: Bookmark these test sites and run quick checks whenever you notice unusual torrent speeds or connection behavior.Troubleshooting Common Issues
ISP Throttling Despite Using VPN
**Problem**: Download speeds drop significantly even with VPN enabled. **Likely Cause**: ISP is using deep packet inspection or VPN traffic shaping. **Fix**: 1. Switch to a different VPN protocol (OpenVPN to WireGuard) 2. Enable obfuscation features in your VPN client 3. Try connecting to different server locations 4. Use port forwarding if your VPN provider supports itReceiving Copyright Notices While Protected
**Problem**: DMCA notices arrive despite using privacy tools. **Likely Cause**: VPN connection dropped or DNS leaks exposed real IP address. **Fix**: 1. Enable kill switch in your VPN client settings 2. Configure DNS leak protection or use VPN's DNS servers 3. Test for IP/DNS leaks at ipleak.net before torrenting 4. Bind your torrent client to the VPN network interface onlyTorrent Client Won't Connect to Peers
**Problem**: No seeds/peers connecting, downloads stuck at 0%. **Likely Cause**: ISP blocking torrent ports or VPN blocking P2P traffic. **Fix**: 1. Change torrent client port to a random high number (49152-65535) 2. Verify your VPN allows P2P on the selected server 3. Enable UPnP/NAT-PMP in router settings 4. Forward the torrent port manually in router configurationInconsistent Connection Monitoring
**Problem**: Uncertain whether ISP can see torrent activity. **Likely Cause**: Incomplete understanding of current protection status. **Fix**: 1. Use network monitoring tools like Wireshark to analyze traffic 2. Check torrent client's peer list for your real IP address 3. Verify all torrent traffic routes through VPN using netstat commands 4. Monitor bandwidth usage patterns in ISP account portalSlow Torrent Performance
**Problem**: Extremely slow download speeds compared to direct downloads. **Likely Cause**: ISP traffic shaping or suboptimal VPN configuration. **Fix**: 1. Test speeds with VPN disabled (use legal torrents only) 2. Adjust connection limits in torrent client settings 3. Try different VPN server locations closer to seeders 4. Enable encryption in torrent client preferencesFrequently Asked Questions
Q: Can my ISP see what specific files I'm downloading via torrent?
A: Your ISP can see that you're using BitTorrent protocol and the IP addresses you're connecting to, but they cannot see the actual file names or content without deep packet inspection. However, they can identify torrent traffic patterns and may receive DMCA notices from copyright holders who monitor torrent swarms.
Q: Will using a VPN completely hide my torrenting activity?
A: Yes, a reliable VPN encrypts all your traffic and routes it through their servers, making your torrenting activity invisible to your ISP. Your ISP will only see encrypted data going to the VPN server, not your actual torrent traffic or the sites you visit.
Q: Can I get in trouble for torrenting legal content?
A: Torrenting legal content is perfectly legal, but your ISP may still throttle your connection due to high bandwidth usage. Some ISPs have policies against any P2P activity regardless of content legality, so using a VPN protects you from potential service restrictions.
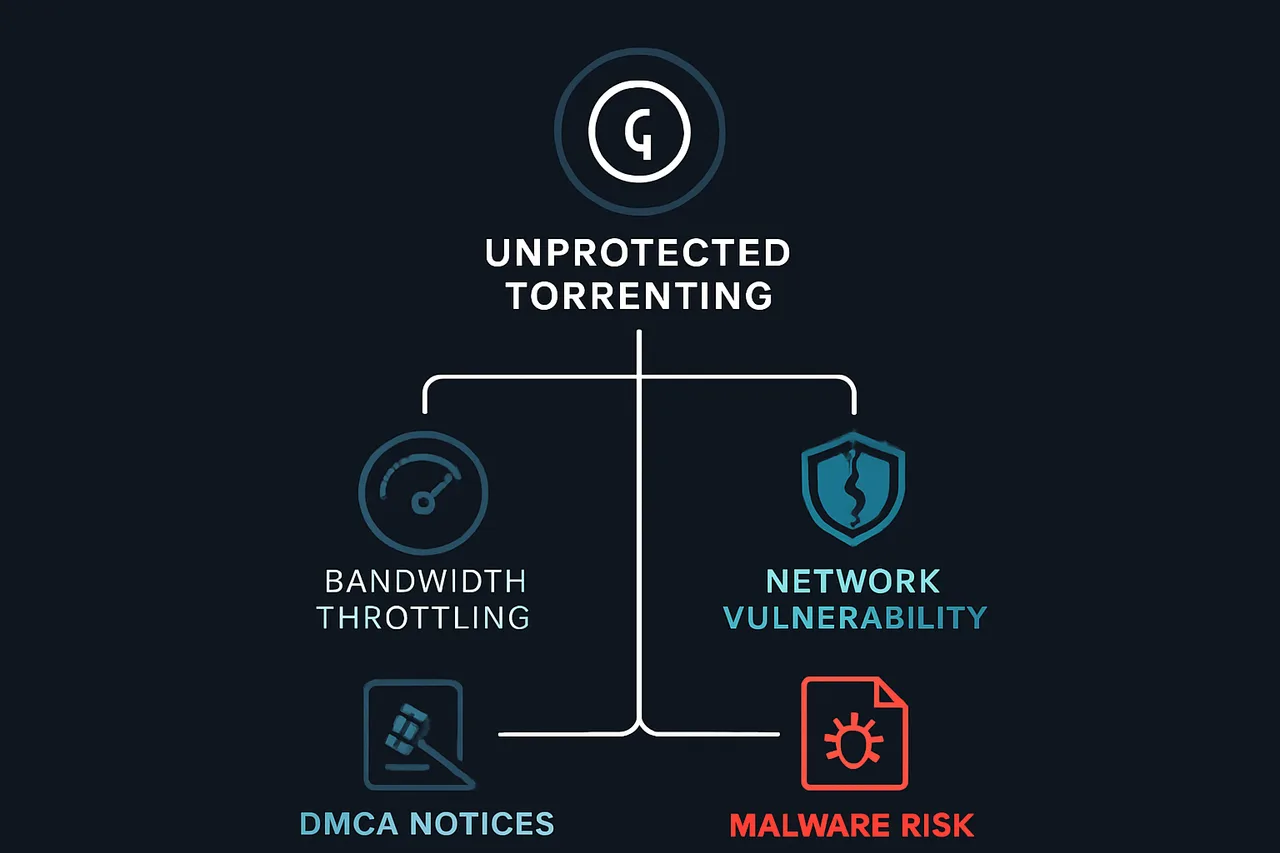
The Real Costs of Unprotected Torrenting: From ISP throttling and DMCA notices to malware exposure and network compromise, the risks extend far beyond detection. Q: How do copyright holders track torrenters if ISPs can't see file names?
A: Copyright holders join torrent swarms directly and log the IP addresses of users downloading their content. They then contact ISPs to identify the account holders behind those IP addresses and send DMCA takedown notices.
Q: Is using public Wi-Fi safer for torrenting than my home internet?
A: No, using public Wi-Fi for torrenting is actually riskier and potentially illegal depending on the network's terms of service. You're also exposing other users on the network to potential legal notices, and your activity can still be traced back to you.
🛡️ Best VPN for Torrenting: ProtonVPN
Secure Core routes traffic through privacy-friendly countries. Based in Switzerland with strong privacy laws. Open-source and independently audited.
[GET_PROTONVPN]✓ 30-day money-back guarantee ✓ Works with all torrent clients ✓ Swiss privacy
Conclusion
Your ISP has significant visibility into your torrenting activities through traffic analysis, bandwidth monitoring, and cooperation with copyright enforcement. While they may not see specific file names, they can easily identify torrent usage patterns and will forward any legal notices directly to you. The most effective protection is using a reputable VPN service that doesn't log your activity and allows P2P traffic. This encrypts your connection and masks your real IP address from both your ISP and copyright monitoring services. Ready to protect your privacy? Check out our comprehensive VPN tier list to find the best service for your needs, or explore our more guides for additional privacy and security tips.